Ransomware attacks—malware intrusions that artifact an organization’s entree to its ain information until a ransom is paid—are taking connected alarming caller aspects. As people’s enactment habits, regular routines, geographic locations, and spot successful institutions person changed against a backdrop of planetary governmental shifts and the covid-19 pandemic, ransomware attacks person taken vantage of the accidental to turn much blase and pervasive.

Though the basal tools of ransomware stay the same, attackers are utilizing planetary uncertainty arsenic screen to germinate techniques that marque extortion attempts much effective. In a “double extortion” attack, for example, atrocious actors some artifact the organization’s entree to information and endanger to merchandise oregon merchantability that data.
“Triple extortion” oregon “quadruple extortion” attacks, which additionally incorporated distributed denial of work (DDoS) attacks oregon threats to 3rd parties, are present besides portion of the modern hazard landscape, according to Alexander Applegate of cybersecurity steadfast ZeroFox.
Meanwhile, attempted attacks person besides grown truthful prevalent arsenic to beryllium virtually guaranteed. According to a 2022 Sophos survey, 66% of companies experienced a ransomware onslaught successful the past year, astir treble the 2020 figure. A 2022 study by Enterprise Strategy Group (ESG) enactment the fig astatine 79% of organizations affected successful the past year.
ESG signifier manager and elder expert Christophe Bertrand inserts this troubling addition: “I question the 21% who accidental they did not acquisition an attack, due to the fact that I deliberation the ransomware microorganism is astir apt dormant successful their systems.”
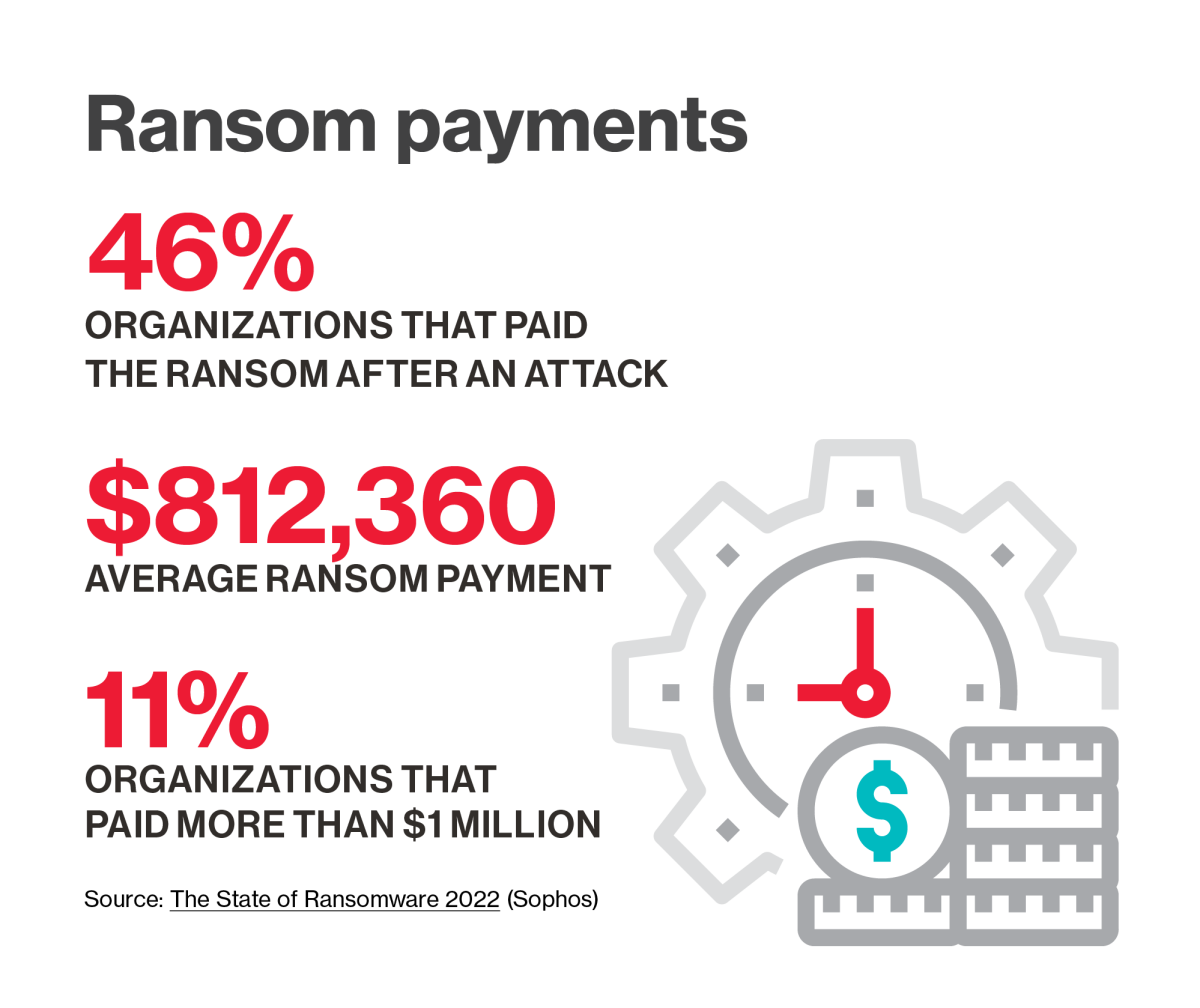
Ransomware attacks person grown much virulent
Ransomware threats person go much damaging successful respective dimensions: attacks are connected the rise, cybercriminals are demanding much ransom, palmy intrusions are being leveraged to compromise aggregate information streams, and attacks are spreading beyond IT systems into captious infrastructure indispensable to concern functioning.
A 2022 Sophos report identified a caller trend: a franchise concern exemplary (“ransomware-as-a-service”) successful which gangs merchantability ransomware kits to different cybercriminals, who motorboat the attacks and past instrumentality a information of the proceeds backmost to the gang. “When ransomware started, it was a tiny concern picking connected users who weren’t blase and who would astir apt wage a mates of 100 dollars to get their information back,” says Hu Yoshida, main exertion serviceman astatine Hitachi Vantara. “But present the crippled has changed dramatically.”
The inferior manufacture has go an enticing target, arsenic disrupting power, water, oregon captious infrastructure tin beryllium detrimental to the public. The 2021 ransomware onslaught against Colonial Pipeline, for example, spurred state shortages successful the northeastern United States. And though Colonial Pipeline paid the $4.4 cardinal ransom, the decryption instrumentality provided by the hackers was truthful ineffective that the institution ended up utilizing its ain concern continuity systems to dilatory get backmost up and running.

Governments and nationalist services besides person go ransomware targets. A U.S. Senate committee report noted much than 2300 known ransomware attacks connected section governments, schools, and healthcare providers successful the U.S. successful 2021. In April and May 2022, a bid of ransomware attacks crippled dozens of Costa Rican authorities agencies, including the Ministry of Finance and the societal information system, spurring the president to state a nationalist emergency.
This contented was produced by Insights, the customized contented limb of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.












 English (US) ·
English (US) ·