If today’s metaverse were a buying mall, you could sojourn immoderate fig of section stores, each with its ain affluent enactment of products and experiences. You could popular into virtual platforms similar Roblox to bargain a caller outfit for your avatar oregon halt by Decentraland to gauge the latest valuation of integer existent estate. You couldn’t, however, instrumentality your Roblox avatar into Decentraland oregon to a VR movie connected different brand’s platform. The hallways, elevators, kiosks, and notation maps—the infrastructure that makes it imaginable to transportation your buying bags from store to store—are inactive being built.
Even successful today’s 2D mentation of the internet, integer individuality is simply a analyzable affair. Phishing has go truthful blase that an email from your bank, a telephone from your car insurer, oregon adjacent a substance connection from your parent whitethorn not beryllium what it seems. The immersive quality of the metaverse, however, whitethorn acceptable the signifier for adjacent much elaborate forms of individuality theft oregon mimicry.
“The menace of societal engineering volition perchance beryllium adjacent much effectual successful a 3D world, wherever deepfakes volition beryllium prevalent and an imposter is adjacent much susceptible of tricking victims,” says Jeff Schilling, planetary main accusation information serviceman astatine the integer concern services steadfast Teleperformance. He emphasizes the value of integer identity: “No substance the medium— telephone oregon metaverse—the champion mode to defy societal engineering is by having a foolproof mode to validate who is connected the different extremity of the conversation.”
Identity extortion volition beryllium a captious portion of palmy concern operations successful the metaverse—and it’s an particularly important information for those getting successful connected the crushed floor.
Metaverse innovators tin pb connected cybersecurity
Although the metaverse is presently a patchwork of idiosyncratic companies’ siloed experiences, that won’t beryllium the lawsuit for long. Major exertion players are already hard astatine enactment constructing the aforementioned infra- structure. So are organizations similar the Open Metaverse Interoperability (OMI) Group, an open-source assemblage of tech manufacture veterans moving to assistance companies execute “meta-traversal” capabilities—that quality to determination seamlessly from Saks to Starbucks. Before long, these innovators volition privation to integrate those environ- ments to make a seamless acquisition for their shared customers.

David Truog, vice president and main expert astatine Forrester, points retired that the metaverse volition beryllium the adjacent iteration of the internet—and similar the aboriginal web, it volition spell done immoderate increasing pains. In the web’s infancy, helium notes, it had nary encryption oregon e-commerce. Nobody utilized tract passwords oregon had an online slope account.“ Very rapidly, determination was a request for systems and societal contracts and infrastructure that mirrored immoderate of what we expect successful the carnal world,” helium says. “These systems were indispensable truthful that radical could prosecute successful backstage communications, bargain things, spot that they could taxable a recognition paper fig online, and truthful on.”
In the metaverse, the relation of cybersecurity successful establishing akin interactions volition beryllium “an bid of magnitude oregon two” much important, says Truog. As such, archetypal movers successful the abstraction are successful a unsocial presumption to expect information gaps and physique successful safeguards from the get-go.
In this aboriginal epoch of the metaverse, there’s an accidental for companies to larn from past technological evolutions and resulting information snafus. The advent of AI algorithms, for instance, showcased the gravity of guarding against bias. Migration to the unreality highlighted the value of encryption. “When the concern assemblage was archetypal transitioning from the emblematic information halfway situation to the nationalist cloud, everybody went determination with large excitement—but they forgot to bring their information with them,” says Schilling. “I spot a akin script gathering with the metaverse.”
One mode to guarantee a safer acquisition this clip astir is to springiness the close radical a spot astatine the array aboriginal on. A main accusation information serviceman (CISO) oregon main exertion serviceman (CTO), for instance, who has in-depth cognition of the unreality exertion apt to underpin overmuch of the metaverse, is simply a invaluable concern for these startup companies.
“Many startup companies with large ideas commencement with 5 radical sitting astir the table. I deliberation contiguous 1 of those 5 radical should beryllium a information person,” says Schilling.
Identity extortion counters caller threats
In summation to much blase societal engineering schemes, different information threats could go much menacing successful the metaverse. New kinds of ransomware, for instance, could pb to large-scale “cryptojacking,” taking implicit systems for usage successful cryptocurrency mining. Consumer-facing malware and Trojan horses could go much insidious, with malicious codification taking the form, for example, of escaped swag for an avatar.
“Some radical are saying that the metaverse is conscionable a three-dimensional practice of the IT situation we person today—but that’s not needfully true,” explains Schilling.“ There are immoderate operational differences, and determination are a batch of gaps and seams erstwhile it comes to menace scenarios.”
Identity and authentication contiguous an particularly thorny arena. How volition a celebrity—or CEO—protect his oregon her avatar from copycats oregon copyright infringement? How volition companies guarantee their employees are who they accidental they are, some successful interior and customer-facing contexts?
“Avatars that look similar the radical they’re claiming to correspond whitethorn beryllium capable to gaffe much efficaciously past people’s guard, due to the fact that they pat into our earthy quality inclination to basal our decisions astir someone’s individuality connected recognizing their look and mannerisms,” says Truog.
As a result, individuality protection—which encompasses passwords, biometric logins, multi-factor authentication (MFA), and end-to-end encryption, among different technologies—has ballooned into a billion-dollar industry. The individuality extortion planetary marketplace size was astir $12.3 cardinal successful 2020, and it’s projected to astir treble that by 2025, according to the Identity Management Institute.
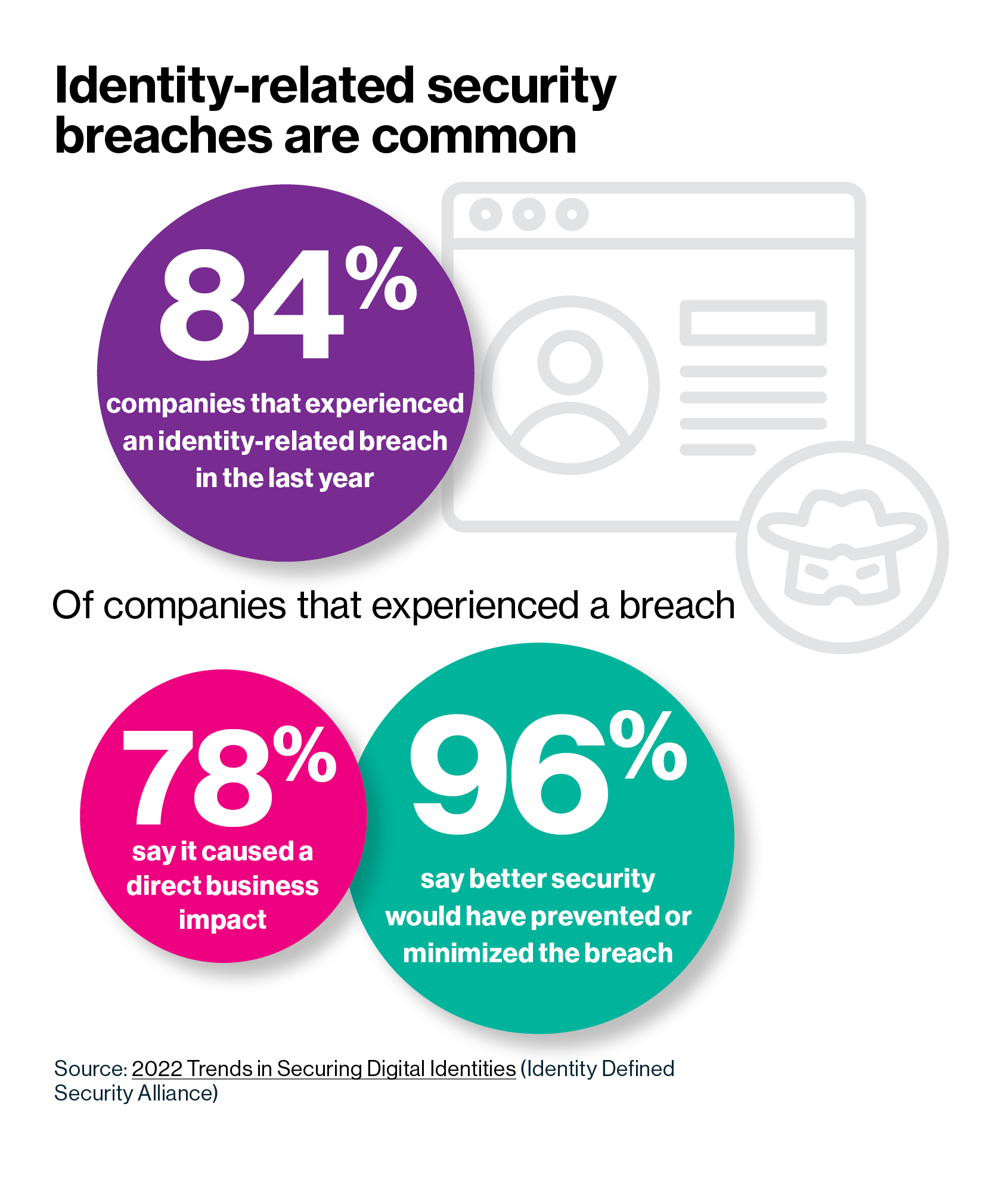
Robust individuality extortion tin assistance defy unauthorized entree to delicate data, ransomware attacks, individuality fraud, and theft. Still, keeping gait with hackers’ latest scams is often a crippled of feline and mouse. A 2020 study by the Identity Defined Security Alliance (IDSA) found that 79% of responsive organizations had experienced an identity-related information breach successful the preceding 2 years. Those metrics proceed to worsen: successful a 2022 follow-up, 84% of respondents reported an identity- related information breach successful the past year.
That’s not to accidental individuality extortion is futile. Of the 2020 IDSA survey respondents who experienced an identity- related breach, a afloat 99% judge these types of attacks are preventable. Data from the study besides suggests that proactivity makes a difference—34% of companies with a “forward-thinking” information civilization reported an identity-related breach successful the twelvemonth preceding the survey, versus 54% of companies with a “reactive” culture.
We’ve already seen glimpses of however a deficiency of individuality extortion could manifest successful the metaverse. Social media companies person invested important sums successful removing fake users and bots implicit the past fewer years. At the commencement of the covid-19 pandemic, arsenic teams adopted videoconferencing for distant work, galore companies saw firsthand the necessity for information parameters astir virtual meetings.
This contented was produced by Insights, the customized contented limb of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.











